Scammers have found a new route for defrauding people. Since Google Maps allows users to submit changes and alterations to…
Tiktok Illegally collecting data sharing
Lorem ipsum dolor sit amet consectet adipisie cing elit sed eiusmod tempor incididunt on labore et dolore. Ut enim ad…
The five devices you need to work anytime
Lorem ipsum dolor sit amet consectet adipisie cing elit sed eiusmod tempor incididunt on labore et dolore. Ut enim ad…
How to learn PHP 10 tips to get you started
Lorem ipsum dolor sit amet consectet adipisie cing elit sed eiusmod tempor incididunt on labore et dolore. Ut enim ad…
The five devices you need to work anytime
Lorem ipsum dolor sit amet consectet adipisie cing elit sed eiusmod tempor incididunt on labore et dolore. Ut enim ad…
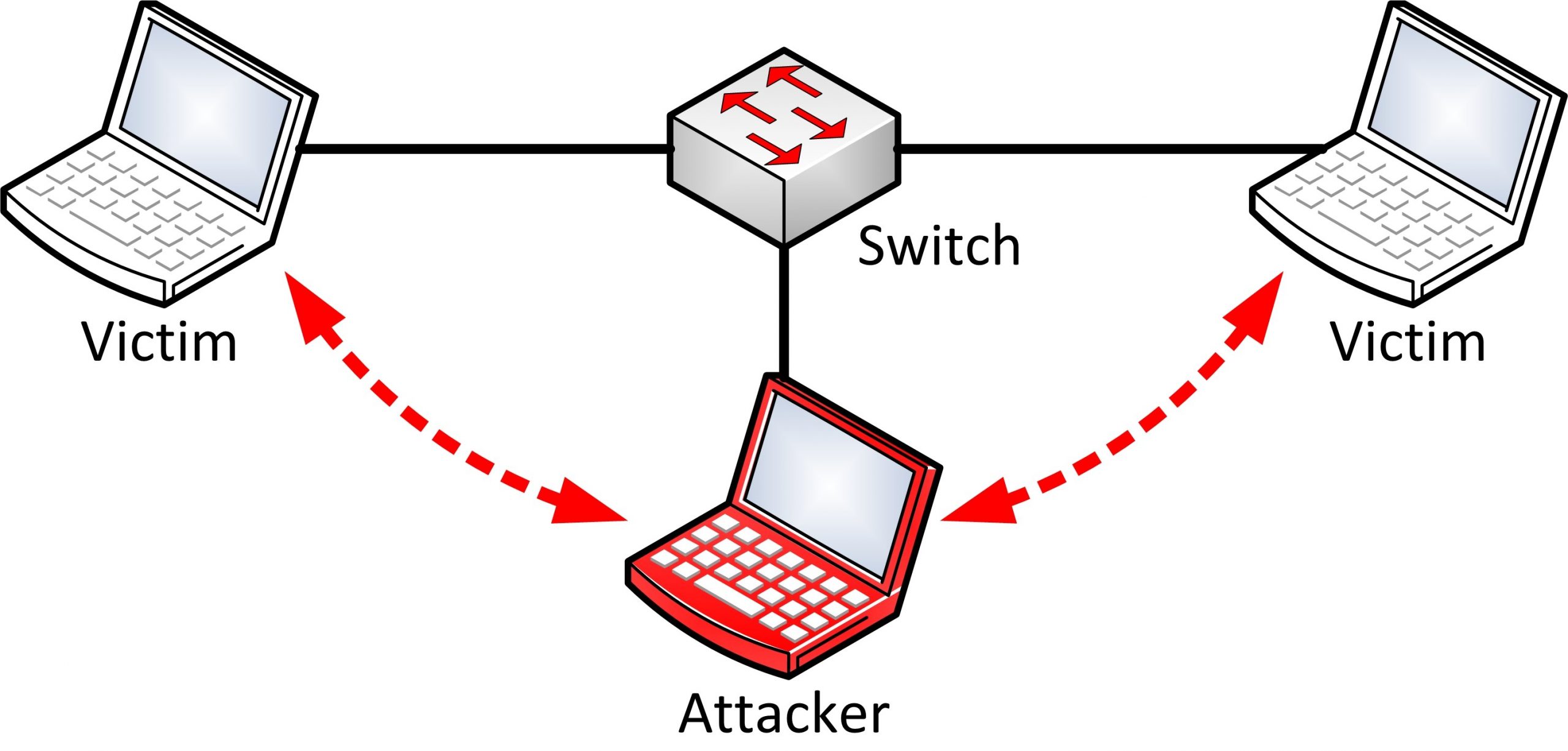
Cyber Security Awareness Month – Spoofing
Spoofing is a fraudulent practice in which a person or malicious program is disguised as a known computer/tablet/phone by cloning…
Cyber Security Awareness Month – Spyware
Spyware is one of the most common threats on the internet. It runs quietly in the background collecting your personal…
Cyber Security Awareness Month – Trojan Horse
A Trojan Horse, or, simply, a trojan, is a kind of malware that hides within computer programs and is designed…
Cyber Security Awareness Month – Ransomware
Ransomware is a type of malware designed to encrypt, erase, or block access to files on a system, until…
Cyber Security Awareness Month – Phishing
Cyber scams are increasing every month and the techniques used are becoming more advanced. Phishing is one of the oldest…